Associate SG and Elastic-IP with EC2
In the previous section, we create an Internet Gateway for our VPC. We also add a static route towards IGW into the Route Table of Subnet 10.10.0.0/24. In this section, we first create a Security Group (SG). The SG allows SSH connection to the EC2 instance and ICMP from the EC2. Then we launch an EC2 and attach the previously configure SG to it. As the last step, we allocate an Elastic IP address (EIP) from the AWS Ipv4 address pool and associate it with the EC instance. When we are done with all the previous steps, we will test the connection. First, we take ssh connection from MyPC to EC2. Then, we ping MyPC from the EC2. We also use AWS Reachability Analyzer to validate the path from IGE to EC2 instance. The last section introduces AWS billing related to this chapter.
Figure 3-20: EC2 Instance, Elastic IP, and Security Group.
Create Security Group
Navigate to the VPC Dashboard. Then select Security Group either from the Security drop-down menu or Resource by Region section.
Figure 3-21: Create Security Group: Phase-1.
In the Security Group window, click the Create Security Group button. Note that the SG DFLT-SECG is the default SG for the default VPC. The two other SGs, in turn, are default SG for our VPCs.
Figure 3-22: Create Security Group: Phase-2.
Fill in the Security Group Name, Description in the Basics details section in Create security group window. Then select our VPC from the VPC drop-down menu.
Figure 3-23: Create Security Group: Phase-3.
Create an Inbound rule that permits SSH from the external host. Then Create an Outbound rule that allows all ICMP traffic towards the external host.
Figure 3-24: Create Security Group: Phase-4.
Figure 3-25 verifies that we have successfully created an SG sg-0e13fbafd10bb59cc.
Figure 3-25: Create Security Group: Phase-5.
When we create an SG, we named it NWKT-SGT-No-01. However, it is visible in the Security group name field while the name column is still empty.
Figure 3-26: Create Security Group: Phase-6.
You can give a name by editing the Name field. You can also select the Tags tab and add a new tag with Key/Value pair Name/NWKT-SSH/ICMP-SGT. Click the Save changes button when done.
Figure 3-27: Create Security Group: Phase-7.
Figure 3-28 verifies our changes.
Figure 3-28: Create Security Group: Phase-8.
Example 3-3 shows the SG in table format on AWS CLI. Note that we are using Tags Key/Pair values. As a recap, if we don’t use “--output table” option, the output format is JSON.
aws ec2
describe-security-groups --filters Name=tag:Name,Values=NWKT-SSH/ICMP-SGT
--output table
------------------------------------------------------
| DescribeSecurityGroups |
+----------------------------------------------------+
|| SecurityGroups ||
|+----------------+---------------------------------+|
|| Description
| Permit SSH & Permit
ICMP ||
|| GroupId
| sg-0e13fbafd10bb59cc ||
|| GroupName
| NWKT-SGT-No-01 ||
|| OwnerId
| 123456654321 ||
|| VpcId
| vpc-04ef72cc79a73f82e ||
|+----------------+---------------------------------+|
||| IpPermissions |||
||+-------------------------------+----------------+||
||| FromPort | 22
|||
||| IpProtocol | tcp
|||
||| ToPort | 22
|||
||+-------------------------------+----------------+||
|||| IpRanges ||||
|||+---------------------+------------------------+|||
|||| CidrIp |
Description ||||
|||+---------------------+------------------------+|||
|||| 91.152.204.245/32 | SSH
from Home PC ||||
|||| 141.192.166.178/32 | SSH from Home PC-new ||||
|||+---------------------+------------------------+|||
||| IpPermissionsEgress |||
||+------------------------------+-----------------+||
||| FromPort | -1
|||
||| IpProtocol | icmp
|||
||| ToPort | -1
|||
||+------------------------------+-----------------+||
|||| IpRanges ||||
|||+------------------+---------------------------+|||
|||| CidrIp |
91.152.204.245/32 ||||
|||| Description |
ICMP to Home PC ||||
|||+------------------+---------------------------+|||
||| Tags |||
||+-------------+----------------------------------+||
||| Key
| Name |||
||| Value
| NWKT-SSH/ICMP-SGT |||
||+-------------+----------------------------------+||
Example 3-3: Security Groups – Table Output from AWS CLI.
Launch an EC2 Instance
Navigate to the EC2 Dashboard. Then select the Launch instance button.
Figure 3-29: Launch EC2 Instance.
I’m using an Amazon
Linux 2 (figure 3-30), which is one of the free tier Amazon Machine Images
(AMI). Note that free tier doesn’t always mean free. For example, the t2.micro
instance type is free for one year only with a new AWS account. My account is
more than 12 years old, so the t2.micro is not free.
Figure 3-30: Launch EC2 Instance: Phase-1.
Select the t2.micro. Click the Next: Configure Instance Details button.
Figure 3-31: Launch EC2 Instance: Phase-2.
Select the VPC and the Subnet where you want to launch the instance. Leave all other fields with their default options (figures 3-32, 3-33, and 3-34).
Figure 3-32: Launch EC2 Instance: Phase-3.
Figure 3-33: Launch EC2 Instance: Phase-3 continues.
We don’t modify the Storage setting or add Tags. Click Next buttons until you end up on to Configure Security Group page.
Figure 3-34: Launch EC2 Instance: Phase-3 continues.
Choose the Select an existing security group radio button. Then select the SG NWKT-SGT-No-01.
Figure 3-35: Launch EC2 Instance: Phase-4 Security Group Association.
Preview your instance setting before launching it. Define the Key pair name and download it before launching (figure 3-37). You use this keypair name when connecting to an instance.
Figure 3-36: Launch EC2 Instance: Phase-5 Review.
Figure 3-37: Launch EC2 Instance: Phase-6 Key Pair.
The Launch status window shows the instance id (i-0b28af5751def332). It also shows the instructions on how you can connect to an instance.
Figure 3-38: Launch EC2 Instance: Phase-7 Launch Status.
Figure 3-39 shows the information related to our EC2instance.
Figure 3-39: Launch EC2 Instance –Running Instance
Description.
Allocate Elastic IP address from Amazon Ipv4 Pool
Navigate to the EC2 dashboard and select an Elastic IP option from the Security drop-down menu. Select the eu-west-2 Network Border Group. Click the Amazon’s pool of Ipv4 address option. Then click the Allocate button.
Figure 3-41 shows that we have successfully allocated a public Ipv4 address 18.134.62.112. The allocation id is eipalloc-01c7d2a4877a061a7. Next, select the Associate Elastic IP address from the Action drop-down menu.
Figure 3-40: Elastic IP Allocation
Figure 3-41: Elastic IP Allocation.
Select the Instance as a resource type. Select our EC2 instance from the Instance drop-down menu. The Private IP 10.10.10.218 is automatically allocated to the instance by AWS when we created it. This IP is auto-filled on the Private IP address field. You can also allow EIP reassociation in this window. As the last step, click the Associate button.
Figure 3-42: Elastic IP Allocation – EIP to Instance
Association.
After association, you will be notified about the successful association (figure 3-43).
Figure 3-43: Elastic IP Allocation – EIP to Instance
Association.
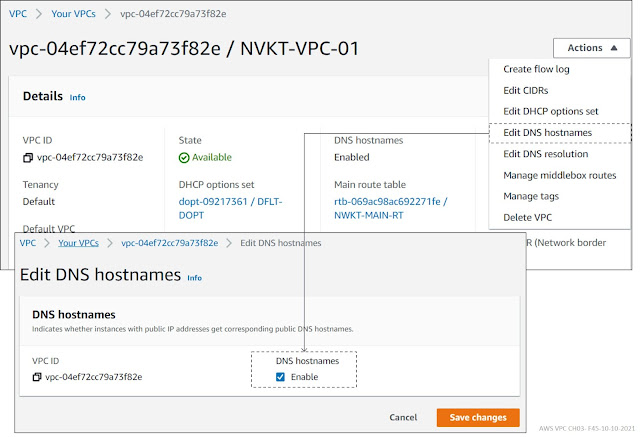
Note that the Public DNS (Ipv4) field is empty. That is because when we created the VPC, we didn’t enable DNS hostname resolution.
Figure 3-44: Elastic IP Allocation – Public DNS.
In order to assign DNS name to instance’s Public IP address, we need to change the VPC DNS setting. Go to the VPC Dashboard and select the VPC. Select the Edit DNS hostnames and click the Save changes button. Note that the VPC window in figure 3-40 is taken after the DNS Resolution change. That is why it shows that that DNS Hostname resolution is enabled.
Figure 3-45: Elastic IP Allocation – EIP to Instance Association.
Figure 4-46 verifies that now we also have a DNS name for the Public IP address. To get instructions on how to connect to the selected instance, click the Connect button. Note that you have to restrict the access permissions of NWKT-EC2-KEY.pem.
Figure 3-46: Elastic
IP Allocation – EIP to Instance Association.
The guide in figure 3-47 shows how to do that on Linux. However, it does not tell how the process is done in Windows.
Figure 3-47: Elastic IP Allocation – EIP to Instance Association.
When you try to connect to EC2 instance when your pem file user access rights are left to their default settings your connection won’t work. You may receive an error notification about Unprotected Private Key File (example 3-4).
C:\folder-1\folder-2\AWS\Chapter-3>ssh
-i "NWKT-KEY-EC2.pem"
ec2-user@ec2-18-134-62-112.eu-west-2.compute.amazonaws.com
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY
FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions
for 'NWKT-KEY-EC2.pem' are too open.
It is
required that your private key files are NOT accessible by others.
This
private key will be ignored.
Load key
"NWKT-KEY-EC2.pem": bad permissions
ec2-user@ec2-18-134-62-112.eu-west-2.compute.amazonaws.com:
Permission denied (publickey,gssapi-keyex,gssapi-with-mic).
Example 3-4: SSH Connection Failure Due to too Open File Permissions.
In order to change access rights, go to the properties of an NWKT-KEY-EC2.pem and select the Security tab. Figure 3-48 shows that four groups/users have full access to file by default. Click the Advanced button. Next, click the Disable inheritance button.
Figure 3-48: Changing pem File User Access Policy in
Windows – Step-1.
Remove all default users from the permission entry. Then add your account to it with full file permission.
Figure 3-49: Changing pem File User Access Policy in
Windows – Step-2.
After the change, you can connect to your instance.
C:\folder-1\folder-2\AWS\Chapter-3>ssh -i
"NWKT-KEY-EC2.pem"
ec2-user@ec2-18-134-62-112.eu-west-2.compute.amazonaws.com
__| __|_ )
_| (
/ Amazon Linux 2 AMI
___|\___|___|
https://aws.amazon.com/amazon-linux-2/
[ec2-user@ip-10-10-0-218 ~]$
Example 3-5: Successful SSH Connection.
The example below verifies that we also have a connection from the EC2 Instance to the external host 91.152.204.245.
[ec2-user@ip-10-10-0-218 ~]$ ping 91.152.204.245
PING 91.152.204.245 (91.152.204.245) 56(84) bytes of
data.
64 bytes from 91.152.204.245: icmp_seq=1 ttl=102
time=0.885 ms
64 bytes from 91.152.204.245: icmp_seq=2 ttl=102
time=0.844 ms
64 bytes from 91.152.204.245: icmp_seq=3 ttl=102
time=0.913 ms
64 bytes from 91.152.204.245: icmp_seq=4 ttl=102
time=0.976 ms
64 bytes from 91.152.204.245: icmp_seq=5 ttl=102
time=0.902 ms
^C
--- 91.152.204.245 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time
4053ms
rtt min/avg/max/mdev = 0.844/0.904/0.976/0.042 ms
[ec2-user@ip-10-10-0-218 ~]$
Example 3-6: Ping from the EC2 Instance to External Host.
Example 3-7 below
shows the complete Instance information.
C:\folder-1\folder-2\AWS\Chapter-3>aws
ec2 describe-instances --output table
------------------------------------------------------------------------------------
|
DescribeInstances |
+----------------------------------------------------------------------------------+
|| Reservations ||
|+---------------------------------+----------------------------------------------+|
||
OwnerId
| 123456654321 ||
||
ReservationId | r-0edc1be860412bb63 ||
|+---------------------------------+----------------------------------------------+|
|||
Instances |||
||+------------------------+-----------------------------------------------------+||
||| AmiLaunchIndex |
0
|||
||| Architecture |
x86_64
|||
||| ClientToken | |||
||| EbsOptimized |
False
|||
||| EnaSupport |
True
|||
||| Hypervisor |
xen |||
||| ImageId | ami-02f5781cba46a5e8a |||
||| InstanceId |
i-0b282af5751def332 |||
||| InstanceType |
t2.micro |||
||| KeyName | NWKT-KEY-EC2 |||
||| LaunchTime |
2021-10-08T15:37:19.000Z |||
||| PrivateDnsName |
ip-10-10-0-218.eu-west-2.compute.internal |||
||| PrivateIpAddress |
10.10.0.218 |||
||| PublicDnsName |
ec2-18-134-62-112.eu-west-2.compute.amazonaws.com |||
||| PublicIpAddress |
18.134.62.112 |||
||| RootDeviceName |
/dev/xvda |||
||| RootDeviceType |
ebs
|||
||| SourceDestCheck |
True |||
||| StateTransitionReason |
|||
||| SubnetId |
subnet-04af160d1d0aee071 |||
||| VirtualizationType |
hvm |||
||| VpcId | vpc-04ef72cc79a73f82e |||
||+------------------------+-----------------------------------------------------+||
|||| BlockDeviceMappings ||||
|||+--------------------------------------+-------------------------------------+|||
|||| DeviceName | /dev/xvda ||||
|||+--------------------------------------+-------------------------------------+|||
||||| Ebs |||||
||||+--------------------------------+-----------------------------------------+||||
||||| AttachTime | 2021-10-08T15:37:20.000Z |||||
||||| DeleteOnTermination |
True
|||||
||||| Status | attached |||||
||||| VolumeId | vol-0a6d0b7dccab72820 |||||
||||+--------------------------------+-----------------------------------------+||||
||||
CapacityReservationSpecification ||||
|||+-------------------------------------------------------------+--------------+|||
|||| CapacityReservationPreference | open
||||
|||+-------------------------------------------------------------+--------------+|||
||||
CpuOptions ||||
|||+-----------------------------------------------------------+----------------+|||
|||| CoreCount
| 1 ||||
|||| ThreadsPerCore |
1 ||||
|||+-----------------------------------------------------------+----------------+|||
||||
HibernationOptions ||||
|||+---------------------------------------------+------------------------------+|||
|||| Configured | False ||||
|||+---------------------------------------------+------------------------------+|||
||||
Monitoring ||||
|||+-------------------------------+--------------------------------------------+|||
|||| State | disabled ||||
|||+-------------------------------+--------------------------------------------+|||
||||
NetworkInterfaces ||||
|||+------------------------+---------------------------------------------------+|||
|||| Description |
Primary network interface ||||
|||| InterfaceType |
interface ||||
|||| MacAddress |
02:cb:a0:af:b7:a0 ||||
|||| NetworkInterfaceId |
eni-07f8f9b7ff3a91f2c ||||
|||| OwnerId | 017857243309 ||||
|||| PrivateDnsName |
ip-10-10-0-218.eu-west-2.compute.internal ||||
|||| PrivateIpAddress |
10.10.0.218 ||||
|||| SourceDestCheck |
True
||||
|||| Status | in-use ||||
|||| SubnetId |
subnet-04af160d1d0aee071 ||||
|||| VpcId | vpc-04ef72cc79a73f82e ||||
|||+------------------------+---------------------------------------------------+|||
|||||
Association |||||
||||+----------------+---------------------------------------------------------+||||
||||| IpOwnerId
| 123456654321
|||||
||||| PublicDnsName | ec2-18-134-62-112.eu-west-2.compute.amazonaws.com |||||
||||| PublicIp
| 18.134.62.112 |||||
||||+----------------+---------------------------------------------------------+||||
||||| Attachment |||||
||||+------------------------------+-------------------------------------------+||||
||||| AttachTime | 2021-10-08T15:37:19.000Z |||||
||||| AttachmentId | eni-attach-06e4d5fc3698f08f6 |||||
||||| DeleteOnTermination |
True
|||||
||||| DeviceIndex | 0 |||||
||||| Status | attached |||||
||||+------------------------------+-------------------------------------------+||||
||||| Groups |||||
||||+-------------------------+------------------------------------------------+||||
||||| GroupId | sg-0e13fbafd10bb59cc |||||
||||| GroupName |
NWKT-SGT-No-01 |||||
||||+-------------------------+------------------------------------------------+||||
|||||
PrivateIpAddresses |||||
||||+---------------------+----------------------------------------------------+||||
||||| Primary |
True
|||||
||||| PrivateDnsName |
ip-10-10-0-218.eu-west-2.compute.internal |||||
||||| PrivateIpAddress |
10.10.0.218 |||||
||||+---------------------+----------------------------------------------------+||||
|||||| Association ||||||
|||||+----------------+-------------------------------------------------------+|||||
|||||| IpOwnerId
| 123456654321 ||||||
|||||| PublicDnsName |
ec2-18-134-62-112.eu-west-2.compute.amazonaws.com ||||||
|||||| PublicIp
| 18.134.62.112 ||||||
|||||+----------------+-------------------------------------------------------+|||||
|||| Placement ||||
|||+--------------------------------------------+-------------------------------+|||
|||| AvailabilityZone | eu-west-2c ||||
|||| GroupName | ||||
|||| Tenancy | default ||||
|||+--------------------------------------------+-------------------------------+|||
||||
SecurityGroups ||||
|||+-------------------------+--------------------------------------------------+|||
|||| GroupId | sg-0e13fbafd10bb59cc ||||
|||| GroupName |
NWKT-SGT-No-01 ||||
|||+-------------------------+--------------------------------------------------+|||
|||| State ||||
|||+-------------------------------+--------------------------------------------+|||
|||| Code | 16 ||||
|||| Name | running ||||
|||+-------------------------------+--------------------------------------------+|||
|||| Tags ||||
|||+---------------------+------------------------------------------------------+|||
|||| Key | Name
||||
|||| Value |
NWKT-EC2-Front-End ||||
|||+---------------------+------------------------------------------------------+|||
Example 3-7: Complete EC2 Instance Information.
Reachability Analyzer
AWS Reachability Analyzer is a tool for troubleshooting reachability problems. We can use it for monitoring the path status between two objects in our VPC. In this section, we verify the path status from the Internet Gateway Endpoint to EC2 Instance NWKT-EC2-Front-End. You can find the Reachability Analyzer from the VPC Dashboard’s Reachability drop-down menu. Click the Create and analyze path button.
Figure 3-50: Reachability Analyzer.
Fill in the name Tag field. Then select the Internet Gateways as Source type. Select our IGW from the Source drop-down menu. The Destination type is Instance. Choose our EC2 instance from the Destination drop-down menu. The inbound security group associated with the EC2 instance allows only SSH connection. SSH use the destination port is 22, and the transport protocol is TCP. Click Create and analyze path button after filling all fields.
Figure 3-51: Reachability Analyzer – Create and Analyze
Path.
Figure 3-52 shows the progress of Reachability status. The Reachability status field turns to Reachable, and the State field shows Succeeded.
Figure 3-52: Reachability Analyzer – Create and Analyze
Path.
Click the Analysis ID nia-08614cd6da8ad0a77 in order to see the visual path representation. Figure 3-53 shows that the path from the Internet GW to EC2 instance first goes through the NACL and then through the SGT.
Figure 3-53: Reachability Analyzer – Visual View.
Billing
The last but not least subject is billing. Figure 3-54 summarizes the cost components for our example environment. Note that AWS charges $0.1 per Path Analysis. Running t2.micro is not expensive. It has been running for 61 hours which costs only 0.81$. It means approximately 10 €/month.
Figure 3-54: Billing.



































Nice blog. Thank For sharing Valuable Information
ReplyDeleteBest AWS Training Online
AWS Online Training Course